In today’s digital age, security is of utmost importance, especially when it comes to accessing and managing remote systems. This is where SSH, or Secure Shell, comes into play. Secure Shell is a network protocol that provides a secure way for users, particularly system administrators, to access a computer over an unsecured network. In this comprehensive guide, we will delve into the world of SSH, exploring its functionalities, use cases, and security measures.
Understanding SSH
SSH, also known as Secure Socket Shell, is a suite of utilities that implement the Secure Shell protocol. Designed to replace insecure terminal emulation or login programs such as Telnet, rlogin, and rsh. By using SSH, users can establish encrypted data communications between two computers connecting over an open network, like the Internet. This ensures that sensitive information remains protected from unauthorized access.
How Does SSH Work?
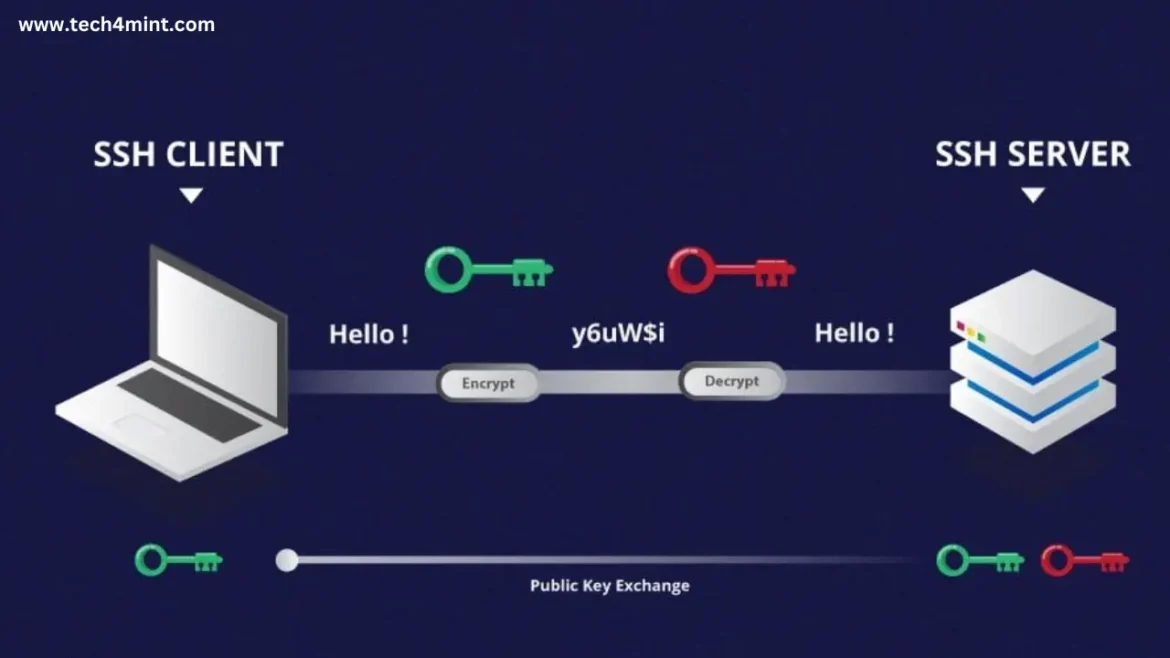
At its core, SSH employs a client-server model, connecting a Secure Shell client application with an SSH server. The client application displays the session, while the server runs the session. Secure Shell implementations often support application protocols used for terminal emulation or file transfers. Additionally, Secure Shell can create secure tunnels for other application protocols, enabling the secure execution of X Window System graphical sessions remotely.
SSH operates on the standard Transmission Control Protocol (TCP) port 22 by default. When establishing a connection for the first time, the user is prompted to verify the remote host’s public key fingerprint. Once you approve it, store the host key in the known_hosts file of the local system, enabling future connections without requiring further approvals.
Use Cases of SSH
SSH is a versatile tool with numerous applications across various industries. Network administrators widely use it to remotely manage systems and applications. Some common use cases of Secure Shell include:
- Secure Remote Access: SSH allows users to securely access SSH-enabled network systems or devices, both manually and through automated processes. It provides a secure and interactive environment for remote administration.
- File Transfer: Secure Shell facilitates secure file transfers between computers. It replaces traditional protocols like FTP and RCP, ensuring the confidentiality and integrity of transferred data.
- Command Execution: SSH enables the secure issuance of commands on remote devices or systems. It allows administrators to execute commands remotely, streamlining management tasks.
- Network Infrastructure Management: SSH is extensively used for the secure management of routers, server hardware, virtualization platforms, operating systems, and other network infrastructure components.
- Secure Tunneling: SSH tunneling, also known as Secure Shell port forwarding, allows users to establish secure tunnels between local and remote hosts. This technique enables applications on the local host to access remote resources directly.
Security Features of SSH
Security is a paramount concern when it comes to remote access and management. Secure Shell provides robust security features to ensure the confidentiality and integrity of data. Some key security aspects of SSH include:
- Strong Authentication: SSH offers both password authentication and public key authentication. While passwords can be used, SSH primarily relies on public key pairs to authenticate hosts to each other, enhancing security.
- Encryption: All traffic transmitted over Secure Shell is encrypted, guaranteeing the privacy of user actions. Whether it’s transferring files, browsing the web, or running commands, all actions are protected.
- Secure Key Management: SSH uses a unique public key pair for each host in communication. This ensures that the local and remote machines authenticate separately. Proper key management is crucial to maintaining control over access to resources.
- Secure Shell Traffic: SSH is built on secure protocols and encryption algorithms. The current version, SSH-2, uses the Diffie-Hellman key exchange and message authentication codes to improve security.
The History of SSH
Secure Shell has a rich history dating back to 1995 when it was first introduced by Tatu Ylönen, a researcher at the Helsinki University of Technology. The developers later found vulnerabilities in SSH-1, and now consider it deprecated. The Internet Engineering Task Force (IETF) adopted SSH-2, the current version, as a Standards Track specification in 2006. It addressed the flaws of SSH-1 and introduced stronger security measures.
SSH Implementations
Various computing platforms have implemented Secure Shell, an open protocol. The most commonly used implementation is OpenSSH, which is found on Linux, Unix, Mac, and other BSD-based operating systems. OpenSSH is an open-source project that provides a suite of Secure Shell utilities.
Another popular implementation is PuTTY, originally designed for Windows but now available for macOS and Unix/BSD as well. Many people widely recognize PuTTY for its user-friendly interface and extensive functionality.
SSH Commands and Utilities
Secure Shell offers a range of commands and utilities to execute various functions. While there are graphical implementations available, Secure Shell commands are typically invoked from the command line or executed as part of scripts. Some essential Secure Shell commands include:
- SSH: The Secure Shell command establishes a connection to a remote host. It prompts the user for authentication credentials and allows for remote terminal sessions and command execution.
- SSHD: The Secure Shell daemon initiates the Secure Shell server, which listens for incoming connection requests and enables authorized systems to connect.
- SSH-Keygen: This command generates a new authentication key pair for Secure Shell. Users automate logins, implement single sign-on (SSO), and authenticate hosts using it.
- SSH-Copy-Id: This utility copies, installs, and configures a Secure Shell key on a server, enabling passwordless logins and SSO.
- SSH-Agent and SSH-Add: These utilities work together to manage identity keys and enable SSO using Secure Shell.
Secure Shell Tunneling: Enhancing Security and Connectivity
Secure Shell tunneling, also known as Secure Shell port forwarding, is a powerful technique that allows users to establish secure tunnels between local and remote hosts. This enables applications on the local host to access resources on the remote host directly. Secure Shell tunneling is a valuable tool for IT administrators and developers alike, as it provides enhanced security and connectivity options.
Security Considerations and Best Practices
While Secure Shell is a secure protocol, it is essential to follow best practices to maintain a secure environment. Some key considerations include:
- Host Key Management: Organizations should have processes in place to manage host keys stored on client systems. This prevents unauthorized access and ensures control over resources.
- Secure Scripting: When incorporating Secure Shell commands into scripts or programs, developers must be cautious. Including user IDs and passwords in scripts may expose credentials to attackers with access to source code.
- Key Management: Proper centralized creation, rotation, and removal of Secure Shell keys are crucial. Without effective key management, organizations may lose control over resource access and compromise security.
SSH vs. Telnet: Choose Security Over Vulnerability
Terminal emulation and remote access commonly use Telnet, an early internet application protocol. However, Telnet lacks the security measures provided by Secure Shell. Secure Shell offers similar functionalities to Telnet but with enhanced security through encryption and strong authentication. Strongly recommend prioritizing Secure Shell over Telnet to protect sensitive data and prevent unauthorized access.
Conclusion
In conclusion, Secure Shell, or Secure Shell, is a robust network protocol that provides a secure way to access and manage remote systems. With its strong authentication, encryption, and secure key management, Secure Shell ensures the confidentiality and integrity of data during communication. Whether it’s secure remote access, file transfers, or command execution, Secure Shell is a versatile tool with numerous applications. By following security best practices, organizations can leverage Secure Shell to create a secure and efficient environment for remote administration and resource management.